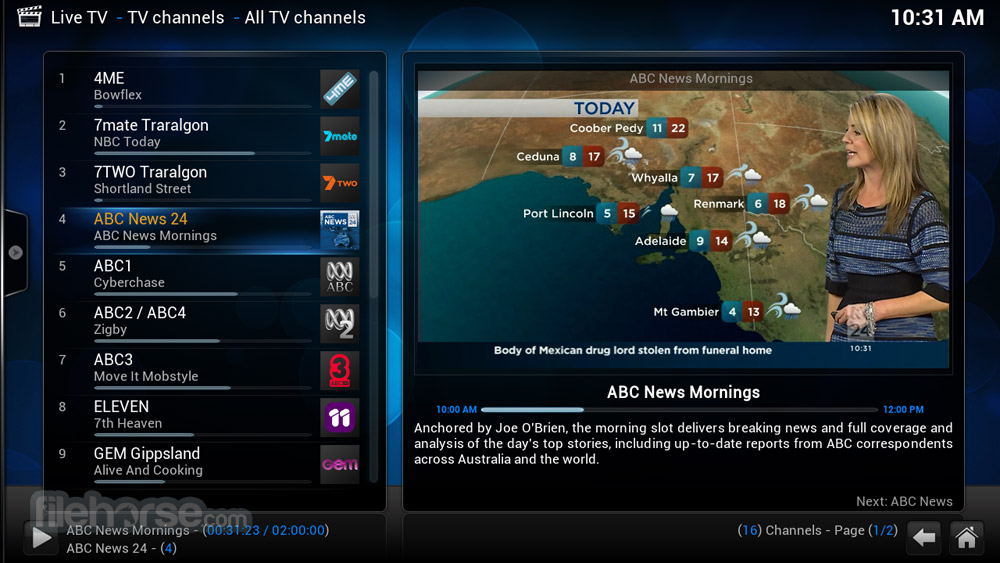
Today I am going to show how to install MACOS Catalina on PC the easy way. Install Hackintosh on your Laptop or PC in easy way. Step by step process to insta. How to Install Kodi for Mac – Kodi 18 Guide. The following step-by-step guide will show you How To Install Kodi for Mac. In this example, we are using a MacBook Pro with macOS Mojave version 10.14.6. Open an Internet browser on your Mac and visit the official Kodi website – 2.
Since 2012, all apps on the Mac App Store must run in an app sandbox, which restricts access to system resources unless explicitly required. The secure sandbox isolates the app and defines access controls, protecting users from malicious code with undesired behaviour.

Here's how to setup a sandbox for an app downloaded from outside the Mac App Store. Remington 1100 shotgun serial numbers.
In my case, I wanted to test out Kodi v17.0 'Krypton' Release Candidate 4 (previously XBMC), an open-source, cross-platform media centre software. I also installed a Kodi Add-on from an 'untrusted source,' which sounds dangerous, doesn't it?
Enter, sandbox! My goal was to prevent Kodi from reading my files, and writing files in locations I did not expect. This goes a long way to securing the system but does not guarantee that you are 'protected'!
Information on sandboxing is rather sparse, but I found two great sources:
- Paolo Fabio Zaino's Blog - How to run your Applications in a Mac OS X sandbox to enhance security and Maximum security and privacy using Mac OS sandbox and Tor browser bundle
- Mozilla's Sandbox OS/X rule set with a detailed Apple's Sandbox Guide v1.0 PDF
Also, your mac also comes with pre-configured sandbox rules found in /usr/share/sandbox/ which are good starting points.
Creating a Sandbox and Running It
To run an app sandboxed, first create a file with the set of rules to permit or deny access to system resources, e.g. file system, network, audio, etc.
In kodi.sb:
Now, instead of running the application directly, run it via Terminal:
Finally, to create a 'shortcut' to sandbox-exec that can be quickly run from Finder / Spotlight, create a file called kodi.command as below. The individual commands can be concatinated into a single line, or you can maintain the line breaks for readability:
Manual Sandbox Testing
Kodi Mac Os Catalina Download
To configure the rules, my process was:
- Initially, deny all access,
- Run Kodi (which would inevitably fail), and:
- Inspect the console output,
- Inspect the Kodi log files and via Console,
- And also view the open files and ports in Activity Monitor (screen shot below).
- Add individual
allowpermissions one at a time, until I get the functionality I expect.
Via Activity Monitor, double click on an app and select Open Files and Ports:
I didn't test everything, and I intentionally did not want Kodi to access my filesystem. You might want to change this behaviour, e.g. add your movies and music folders. I also see Kodi is trying to access /Users/[[username]]/Library/Saved Application State/org.xbmc.kodi.savedState/ but I was simply too lazy to add it.
Kodi Mac Os Catalina Island
Sandbox Rules
To briefly explain the rules:
deny default- deny everything by default.allow network- allows network access.allow iokit-open- access to device drivers, required for Core Image and OpenGL.allow file-read-metadata- without which, no ability to list directories (ls).allow mach* sysctl-read- to get to system info in read mode.(allow ipc-posix-shm (ipc-posix-name-regex '^AudioIO'))- it took me the longest time to enable audio, turns out AudioIO is implemented using shared memory.(allow process-exec (regex '/Applications/Kodi.app'))- allow the Kodi process, and any child processes, to run.(allow file-read-data (literal '/dev/urandom'))- to avoid the errorError in GnuTLS initialization: Failed to acquire random data, configured to be an exact match (literal, compare withregexbelow).(allow file-read-data (regex.. - read access to system library files and the Kodi.app contents itself:- The regex pattern
^means 'starting with' i.e. allow read only access to files and folders starting with/System/Library/. - You can add other folders here, e.g.
'^/usr/lib/.*.dylib$'to access user libraries. The$means 'ending with' and is an example of being explicit! - Or the movies, music and
org.xbmc.kodi.savedStatefolders mentioned above.
- The regex pattern
(allow file-write* file-read-data (regex.. - allow write access to:Logsfolder.Application Supportwhere add-ons, preferences and databases are stored.
Conclusion
MacOS has an extremely granular sandboxing capability, courtesy of BSD, and is enabled by default for apps from the Mac App Store.
However, to sandbox any other application, it's rather involved and poorly documented. I hope the simplified explanation and sample rules above help you.
This only supports Azure Resource Manager objects, to support objects without Azure Resource Manager, see Connect with Windows Desktop (classic) client. This does not support the RemoteApp and Desktop Connections (RADC) client or the Remote Desktop Connection (MSTSC) client. Azure remote desktop client.
Description Use the Microsoft Remote Desktop app to connect to a remote PC or virtual apps and desktops made available by your admin. The app helps you be productive no matter where you are. Getting Started Configure your PC for remote access first. You can control a remote PC by using a Microsoft Remote Desktop client. The client can run on almost any device, including on your mobile smartphone. The client gives you the same powers you would have if you could reach the PC's keyboard. Through the client, you can. 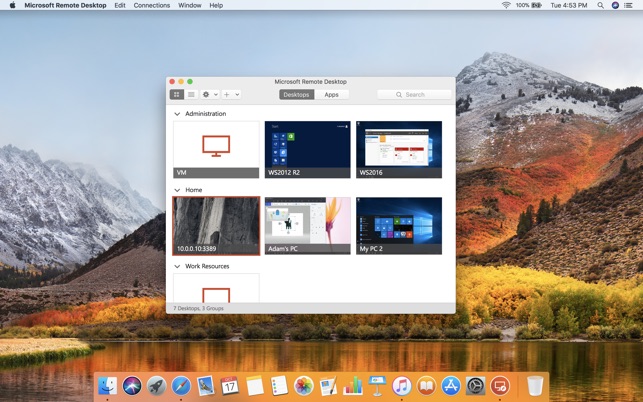
How To Install Git On Macos Catalina
Updated 9 Feb: allow read access to /usr/share/zoneinfo for the time to be displayed correctly based on the configured time zone.
Update 4 Mar: use sandbox-exec -p profile-string instead, to avoid the dependency on an external .sb file.
Kodi Para Mac Os Catalina
Update 26 Mar: fixed a small 'bug' where I refer to sandbox_exec instead of sandbox-exec.
