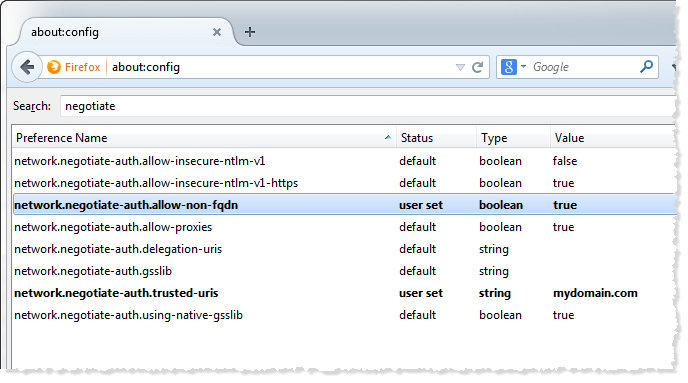
Using Kerberos implies that your client's browser must be configured properly! Depending upon which browser your clients use, you have to set up the Kerberos configuration in a different way. Users can enable Kerberos single sign-on (SSO) authentication using preference in their browser profile but it's also possible to set the default for all Firefox users on the system. During my ApacheCon talkthis year, one of the questions from the audience focused on. I am deploying Linux/Firefox on a corporate Kerberos network. I followed this Kerberos-on-Firefox procedure but still Firefox does not connect via the company's Kerberos. I am using Firefox 3.0.18 on RedHat EL Server 5.5. Here is what I did: Run kinit on the command line to create a Kerberos ticket; Check with klist: the ticket is valid until tomorrow, service principal is krbtgt/DC. Restart Firefox from that shell, and visit the website where Kerberos authentication is failing. Check the /tmp/moz.log file for error messages with nsNegotiateAuth in the message. There are several common errors that occur with Kerberos authentication.
What is Azure Active Directory Seamless Single Sign-On?
Azure Active Directory Seamless Single Sign-On (Azure AD Seamless SSO) automatically signs users in when they are on their corporate devices connected to your corporate network. When enabled, users don't need to type in their passwords to sign in to Azure AD, and usually, even type in their usernames. This feature provides your users easy access to your cloud-based applications without needing any additional on-premises components.
Seamless SSO can be combined with either the Password Hash Synchronization or Pass-through Authentication sign-in methods. Seamless SSO is not Super smash flash 2 v0 7 online game. applicable to Active Directory Federation Services (ADFS).
SSO via primary refresh token vs. Seamless SSO
For Windows 10, Windows Server 2016 and later versions, it’s recommended to use SSO via primary refresh token (PRT). For windows 7 and 8.1 it’s recommended to use Seamless SSO.Seamless SSO needs the user's device to be domain-joined, but it is not used on Windows 10 Azure AD joined devices or hybrid Azure AD joined devices. SSO on Azure AD joined, Hybrid Azure AD joined, and Azure AD registered devices works based on the Primary Refresh Token (PRT)
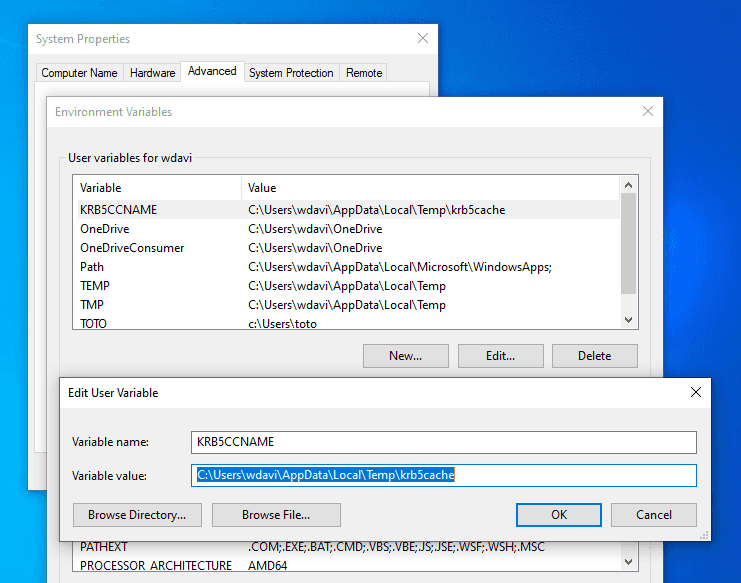
SSO via PRT works once devices are registered with Azure AD for hybrid Azure AD joined, Azure AD joined or personal registered devices via Add Work or School Account.For more information on how SSO works with Windows 10 using PRT, see: Primary Refresh Token (PRT) and Azure AD Best eyebrow pencil review.
Key benefits
- Great user experience
- Users are automatically signed into both on-premises and cloud-based applications.
- Users don't have to enter their passwords repeatedly.
- Easy to deploy & administer
- No additional components needed on-premises to make this work.
- Works with any method of cloud authentication - Password Hash Synchronization or Pass-through Authentication.
- Can be rolled out to some or all your users using Group Policy.
- Register non-Windows 10 devices with Azure AD without the need for any AD FS infrastructure. This capability needs you to use version 2.1 or later of the workplace-join client.
Feature highlights
- Sign-in username can be either the on-premises default username (
userPrincipalName) or another attribute configured in Azure AD Connect (Alternate ID). Both use cases work because Seamless SSO uses thesecurityIdentifierclaim in the Kerberos ticket to look up the corresponding user object in Azure AD. - Seamless SSO is an opportunistic feature. If it fails for any reason, the user sign-in experience goes back to its regular behavior - i.e, the user needs to enter their password on the sign-in page.
- If an application (for example,
https://myapps.microsoft.com/contoso.com) forwards adomain_hint(OpenID Connect) orwhr(SAML) parameter - identifying your tenant, orlogin_hintparameter - identifying the user, in its Azure AD sign-in request, users are automatically signed in without them entering usernames or passwords. - Users also get a silent sign-on experience if an application (for example,
https://contoso.sharepoint.com) sends sign-in requests to Azure AD's endpoints set up as tenants - that is,https://login.microsoftonline.com/contoso.com/<.>orhttps://login.microsoftonline.com/<tenant_ID>/<.>- instead of Azure AD's common endpoint - that is,https://login.microsoftonline.com/common/<..>. - Sign out is supported. This allows users to choose another Azure AD account to sign in with, instead of being automatically signed in using Seamless SSO automatically.
- Microsoft 365 Win32 clients (Outlook, Word, Excel, and others) with versions 16.0.8730.xxxx and above are supported using a non-interactive flow. For OneDrive, you will have to activate the OneDrive silent config feature for a silent sign-on experience.
- It can be enabled via Azure AD Connect.
- It is a free feature, and you don't need any paid editions of Azure AD to use it.
- It is supported on web browser-based clients and Office clients that support modern authentication on platforms and browsers capable of Kerberos authentication:
Linux Kerberos

| OSBrowser | Internet Explorer | Microsoft Edge | Google Chrome | Mozilla Firefox | Safari |
|---|---|---|---|---|---|
| Windows 10 | Yes* | Yes | Yes | Yes*** | N/A |
| Windows 8.1 | Yes* | Yes**** | Yes | Yes*** | N/A |
| Windows 8 | Yes* | N/A | Yes | Yes*** | N/A |
| Windows 7 | Yes* | N/A | Yes | Yes*** | N/A |
| Windows Server 2012 R2 or above | Yes** | N/A | Yes | Yes*** | N/A |
| Mac OS X | N/A | N/A | Yes*** | Yes*** | Yes*** |
*Requires Internet Explorer version 10 or later.
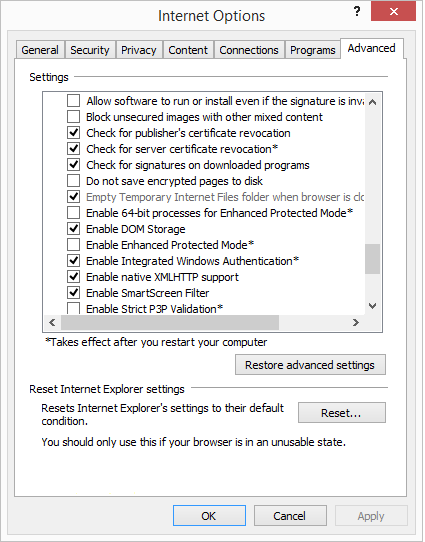
**Requires Internet Explorer version 10 or later. Disable Enhanced Protected Mode.
Linux Kerberos Library
***Requires additional configuration.
Firefox Kerberos
****Requires Microsoft Edge version 77 or later.
Next steps
Firefox Use Windows Auth
- Quick Start - Get up and running Azure AD Seamless SSO.
- Deployment Plan - Step-by-step deployment plan.
- Technical Deep Dive - Understand how this feature works.
- Frequently Asked Questions - Answers to frequently asked questions.
- Troubleshoot - Learn how to resolve common issues with the feature.
- UserVoice - For filing new feature requests.

